What you need to understand is the information processor. When it is exposed to too much of information or traffic which it can’t handle so it blows up.
Rules & Notifications :
AdsBlocker Status : loading...
All Links without this website are modified by Adfly ads. Just Bypass these ads with a single click on "Allow" & "SKIP AD" and then you are able to browse the Main/Original Link. You are valuable to us. There are no fake surveys. All links are same as before. New Modification : With AdsBlocker/PrivacyBlockApp, You can't access this website. Such as PrivacyBadger, AdBlock, UBlock origin etc. Support All Browser with normal mode. Browse happily...
Support Us !
Sunday, September 4, 2022
Download DDoS Tools - How to DDoS Like a Professional Hacker – #1 DDoS Tutorial
What you need to understand is the information processor. When it is exposed to too much of information or traffic which it can’t handle so it blows up.
Download SS7 Framework | Atta_cks Now in your hand with SS7 SigPloit Telephone Network hac_king
An SS7 atta_ck is an exploit that takes advantage of a weakness in the design of SS7 (Signalling System 7) to enable data theft, eavesdropping, text interception and location tracking.

Telecom Signaling Exploitation Framework - SS7, GTP, Diameter & SIP Download, Installation
How to make Metasploit persistent payload or backdoor in termux
How to Recover data from Android Phone Without Unlocking?
I have gone through several forums and discussions and there I found that lots of users were looking for ways on how to enable USB debugging on locked Android phone? and recover data files? This was the most searched topic so I decided to find best way and keep in front of you.
Therefore, I am with this article that will guide you on how to enable USB debugging on Android with black screen or how to remotely enable USB debugging Android and recover android data.
So let’s go through it…
Remember, ADB command is the most powerful way to unlock a broken Android device. Once the command is executed, the data is easily extracted from a broken Android phone with USB debugging.
Here are the steps to follow:
First, install the ADB tool on your computer. You can download from here: ADB Tool
and then extract the zip file on PC.
Normally, ADB requires to communicate phone via USB debugging but, since the USB debugging is turned off on your phone, so here you should boot your device in
Termux with Metasploit and Ngrok Smartphones Hack by Android Smartphone
How to hack android phone using Termux with Metasploit and Ngrok
Requirements: Termux App
Install Metasploit on termux
Port Forwarding using Ngrok in termux
Android Rat - AdoBot a working Android hijacking app with details

Download and Use Termux Zphisher : Advance Phishing Tool For Termux
Install Zphisher Tool in Termux:
To install that zphisher tool in termux you need to install multiple dependency packages as well as you have to upgrade your pre-installed packages.
Just copy the given command and paste it in your termux app and press enter and wait for 2 minutes and the tool will be installed.
cd ; apt update && apt upgrade -y ; apt install git curl wget php -y ; git clone git://github.com/htr-tech/zphisher.git ; cd zphisher
Run ZPhisher Tool in Termux:
Step 1:
After the installation is done you can directly use the below command or if you are using this tool second time then you need to change your directory to the zphisher folder. Type the Below command To Run the Zphisher tool.
bash zphisher.sh
Download iCloud Remover Tool 2020 | Bypass/Unlock iCloud Activation Jailbreak iOS iPhone iPad
SS7 Download and Installation | Hack cell phones using SS7 Attack Flaw

SS7 is vulnerable to hacking and this has been known since 2008. In 2014, the media reported a protocol vulnerability of SS7 by which both government agencies and non-state actors can track the movements of cell phone users from virtually anywhere in the world with a success rate of approximately 70%. In addition, eavesdropping is possible by using the protocol to forward calls and also facilitate decryption by requesting that each caller’s carrier release a temporary encryption key to unlock the communication after it has been recorded. Researchers created a tool (SnoopSnitch) which can warn when certain SS7 attacks occur against a phone and detect IMSI-catchers.
How to Download this SS7 :
How to Bypass iCloud Activation Lock on iPhone/iPad
 Here We disscuss about "How to Bypass iCloud Activation Lock on iPhone/iPad" by 3 Methods. Hope you like it.Comment Your Opinions.
Here We disscuss about "How to Bypass iCloud Activation Lock on iPhone/iPad" by 3 Methods. Hope you like it.Comment Your Opinions.1st Method : Quickest way to bypass iCloud activation.
2nd Method : Bypass iCloud Activation with iCloud Bypass Tool.
3rd Method : How to unlock iCloud activation online.
1st Method : Quickest way to bypass iCloud activation
Tap on the "Home" button and select Wi-Fi Settings. From the Wi-Fi list, click the "i" symbol next to the Wi-Fi network you want to connect to.
In the Wi-Fi setting menu, remove the existing DNS and enter the new DNS according to your location:
IsTheApp is Truely Free Android Spyware Spy App

Feature :
- Multiple Child clients
- Hidden app icon (stealth mode)
- Real-time location.
- Recording calls: incoming/outgoing.
- SMS: received/sent.
- Environment recording.
- Take pictures.
- Keylogger.
- Phishing social network.
- Notifications received: Whatsapp, Instagram, Messenger.
DiskGenius | PartitionGuru Full Version | Best Data Recovery Bootable
Wi-Fi KRACK | How to do? | Tutorial & Downloads
Or, more succinctly, shit’s fucked.
This, obviously, is profoundly complicated stuff.
To help clear things, I spoke to David Gorodyansky, CEO of AnchorFree and HotspotShield, and asked him to explain KRACK like I was five.
Blue Light Filter Software For Windows 7, 8, 8.1, 10

Download Adobe Photoshop CC Latest Crack
How to Send a Spoofed SMS Text Message
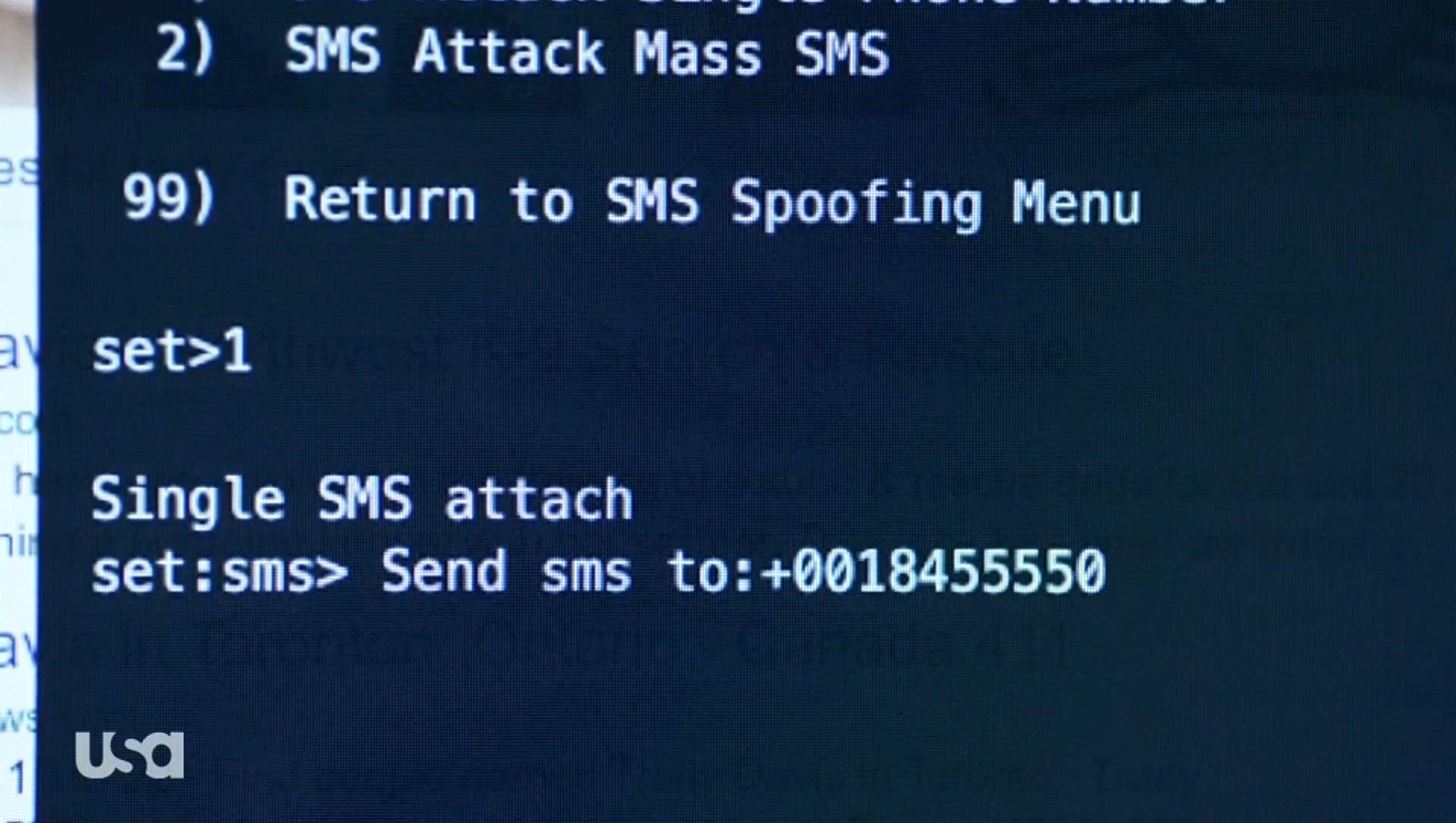
Before Start You must read Earlier post Social Engineering Toolkit ( SET )
The Spoofed Text Message
How to make Trojan Horse | Full Tutorial
Trojan Horse Creation

There are four Steps to make A real Working Trojan Horse using C/C++ , Vmware, Backtrack, Windows Xp.
- Install C/C++ .
- Create & Bundle Trojan Horse.
- Upload to Webserver.
- Social Engineer Trojan Horse and Connect with Metasploit and Netcat.
Email Hacking
Unlimited Whatsapp Account & Others Online Account in one Phone | Clone apps
other social & game accounts online simultaneously on
one phone to separate work and life.😄😄😄
Control Your PC Using Smartphone Bluetooth And WiFi Without Mouse Keyboard
PC Remote : Control Your PC Using Bluetooth And WiFi
- Scroll with two fingers,
- Drag,
- DoubleClick ,
- Right click and Clicks.
Hack email accounts or passwords using session cookies
How To Unlock Android Pattern, Password And Pin Lock Without Factory Reset
Note that this will wipe out all your data saved up in the phone memory.
To avoid losing data therefore, use the method below.
Unlocking or by passing the Android Pattern and pin lock factory resetting or without losing data requires that you have a rooted android device.
Follow Procedure: -------
VMware Workstation Pro Free Download | Crack | Key | Patch [ LATEST ]

VMware Workstation Pro is powerful desktop virtualization software for software developers, testers and enterprise IT professionals that runs multiple operating systems simultaneously on a single PC. VMware Workstation 14 Pro is the easiest, fastest and most reliable way to evaluate new operating systems, software applications and patches, and reference architectures in an isolated and safe virtualized environment. No other desktop virtualization software offers the performance, reliability, and cutting edge features of Workstation Pro. This software is an integral component of any serious technical professional’s toolkit. VMware Workstation Pro 14 takes virtualization to the next level with the broadest operating system support, rich user experience, a comprehensive feature set and high performance.
Pro Website Creation Software Without Coding | Incomedia WebSite X5 Professional 14.0.5.2 [Latest]
Its full offline installer standalone setup of “Incomedia WebSite X5 Professional” for Windows 32 bit 64 bit PC.
Incomedia WebSite X5 Professional is the most versatile and complete software that lets you create attractive, professional and functional websites, blogs and online stores. You don’t need any programming skills to create a website, all you need is a mouse! Incomedia WebSite X5 is easy to use, flexible and open to your customization. You work with a fully-visual intuitive interface, with plenty of previews of your work that are constantly updated in real time.
Quick Fix Hardware & Software issues of any Computer PC / Laptop

Whether you are working on computer at home or at office, troubleshooting PC Common PC Problems and their solutions problems is a part of everyday life. Even though you think that your system is stable and secure, there are thousands of problems that your PC could have like hardware failure, various error messages, malicious software or some time there is only a loose cable.
But wait before you call PC repair experts and pay for tech support.
Here I collect some common PC problems seen by many computer users. I also try my best to give their solutions so that you can probably solve these problems and save your money and time.
Password Protect any Folder without using any Software
With this trick, you can create a secure password protected folder in Windows.
You can use it for any Folder in windows system.
For Password Protect any Folder without using any Software,
Here is the procedure –
- Open Notepad and Copy the below code and past in it.
- Save the notepad file as lock.bat.
Turn any Picture into Windows Icon
Turn Your Personal Pictures into Windows Icons :
An icon is a small picture that represents the program or file or folder with the “.ico” extension. It contains a images, which has various sizes and values of color depth. There are four sizes used for this: 48x48, 32x32, 24x24, and 16x16.
But to create custom icons from your own pictures is a fairly simple process. There are numerous software available to create and modify your own icon. But using online tools, you can create your icon the easiest way and no need to install and learn how to use.
SpyNote (RAT) Download | Hack Android Phone Remotely | Tutorials

DDoS & DoS Hack Tools

This DDoS hack pack tools 2.0 contains the following tools:
- Byte DoS 3.2
- DDoS v2
WhatsApp Sniffer .apk Download for Android | WhatsApp Hacking

Your private chats that took place on your WhatsApp messaging app are not secured because a new Android application called “WhatsApp Sniffer” is a tricky app that can steal your private chats, audios and even videos.Hack WhatsApp Accounts.
Being nosey is part of human nature. Since the beginning of time, mankind has always managed to invent mechanisms to spy on his fellow humans and find out what is being said in conversations that have nothing to do with him.
How to Install Python Packages on Windows

know is that in order to go anywhere and do anything you've got to install packages. Or maybe you don't even know that yet. Take a look at the top of any Python code and you'll likely see a line like this: import thingamajig .
In Python, as with Java and its derivatives, you're always importing some established code into your project. If you're new to Python, new to Command Prompt, and new to anything non-Windows, then you're going to need a hand with that first step.
At the time of this draft, Python 2.7 is the stable install. Download Python from http://www.python.org/ and install it at C:\Python27\ For users with 64-bit systems, the 32-bit version of all software is recommended.
How to Install Python Packages on Windows MSI installer

In Python, as with Java and its derivatives, you're always importing some established code into your project. If you're new to Python, new to Command Prompt, and new to anything non-Windows, then you're going to need a hand with that first step.
How to Install Python Packages on Windows...
Backdoor in Wi-Fi routers lets attacker reset router, get admin

A hacker has found a backdoor to wireless combination router/DSL modems that could allow an attacker to reset the router’s configuration and gain access to the administrative control panel. The attack, confirmed to work on several Linksys and Netgear DSL modems, exploits an open port accessible over the wireless local network.
How can I tell if my FACEBOOK Account info was shared ?
We’re sure you’ve heard of Cambridge Analytica (CA), the controversial company that harvested data from Facebook and then used it in ways that you almost certainly wouldn’t have wanted.
About a month ago, we reported how a CA whistleblower named Christopher Wylie claimed that the company had allegedly:
…exploited Facebook to harvest millions of people’s profiles. And built models to exploit what we knew about them and target their inner demons. That was the basis the entire company was built on.
Were you affected?
R-Undelete Home: Recover Deleted Files on Windows
The Home version of the application is limited to FAT file system recovery, but it will highlight files that it can recover from NTFS file system storage devices as well.
File recovery software comes in handy if you need to recovery files. Maybe you have deleted files by accident, cannot access files after a hard drive crash or unexpected shutdown, or try to recover files after a successful malware attack on a device.
R-Undelete Home can be run as a portable version or a setup version. It is recommended to extract or install the program on disks that you don't need to recover files from as you may make files unrecoverable if you install the program on the disk that you want to recover data from.
R-Undelete
Best Auto Mouse Clicker for Windows
Download Virus/Adware/Malware Free Auto Clicker
Automate your mouse clicking
Fast click mouse cursor automatically in the background for the ultimate convenience
Let the PC do what it should & finish repeated work to get you more time to live your life!
Blogger sign in redirect / loop problem
Can't Sign In After April, 2019
If you cannot sign in to Blogger using your gmail account after April, 2019 - being redirected to the homepage all the time. I believe it's related to the shutdown of Google+.
You can view your blog but cannot go to Blogger to edit it.
If you were able to sign in before April.
My solution for this problem ENDLESS LOOP was to load again this...
Remotely control or Capture Photos in any Android from Another Android by Bluetooth

Hack Any type Android by Malware virus transmitting by TheFatRat
TheFatRat A Massive Exploiting Tool

Hack Database Using Google Firebase 🔥 by Google Dork

Download Spynote 6.5 Free Cracked Licensed For Android Hacking with Tutorial
What is Spynote?
Spy Note is a advanced Remote Administration Tool targeted for Android systems. It’s server is written in Java, and the client controller is written in Visual Basic .NET. After installation on an Android device, Spy Note will automatically remove it’s on-screen icon from the victim’s device.
Features Of SpyNote 6.5
Control with ease You can control all device tools and features.
- Private Binder.
- Private Socket.
- Encrypted Apps.
- Encrypted Connection.
- Stable Installation.
- Port Password.
- Keylogger Offline/Online.
- Accounts Manager.
- Phone Settings.

































